©2024 All Rights Reserved. Created with Phishy
Home
From awareness to action
Secure Every Click
Boost cybersecurity awareness in your team with Phishy’s engaging training and simulations. These tools are crafted to strengthen defenses against sophisticated phishing attacks, ensuring every click contributes to a safer digital environment.
100k+
Global Users
94%
Happy Customers
5+
Major Clients
24/7
Top-Rated Support
UNDERSTANDING THE THREAT
Securing the Human Factor
In the ever-evolving landscape of cyber threats, understanding the human factor is key. Hackers often target individuals, not just systems, crafting sophisticated phishing attacks that can bypass even the most robust technical defenses. At Phishy, we empower individuals and organizations to recognize and respond to these threats effectively.
Hacker's Target
Hackers don't just look for system flaws; they target human errors. Phishy's training is designed to reinforce this human link, making your staff the robust barrier against phishing incursions.
The Art of Phishing
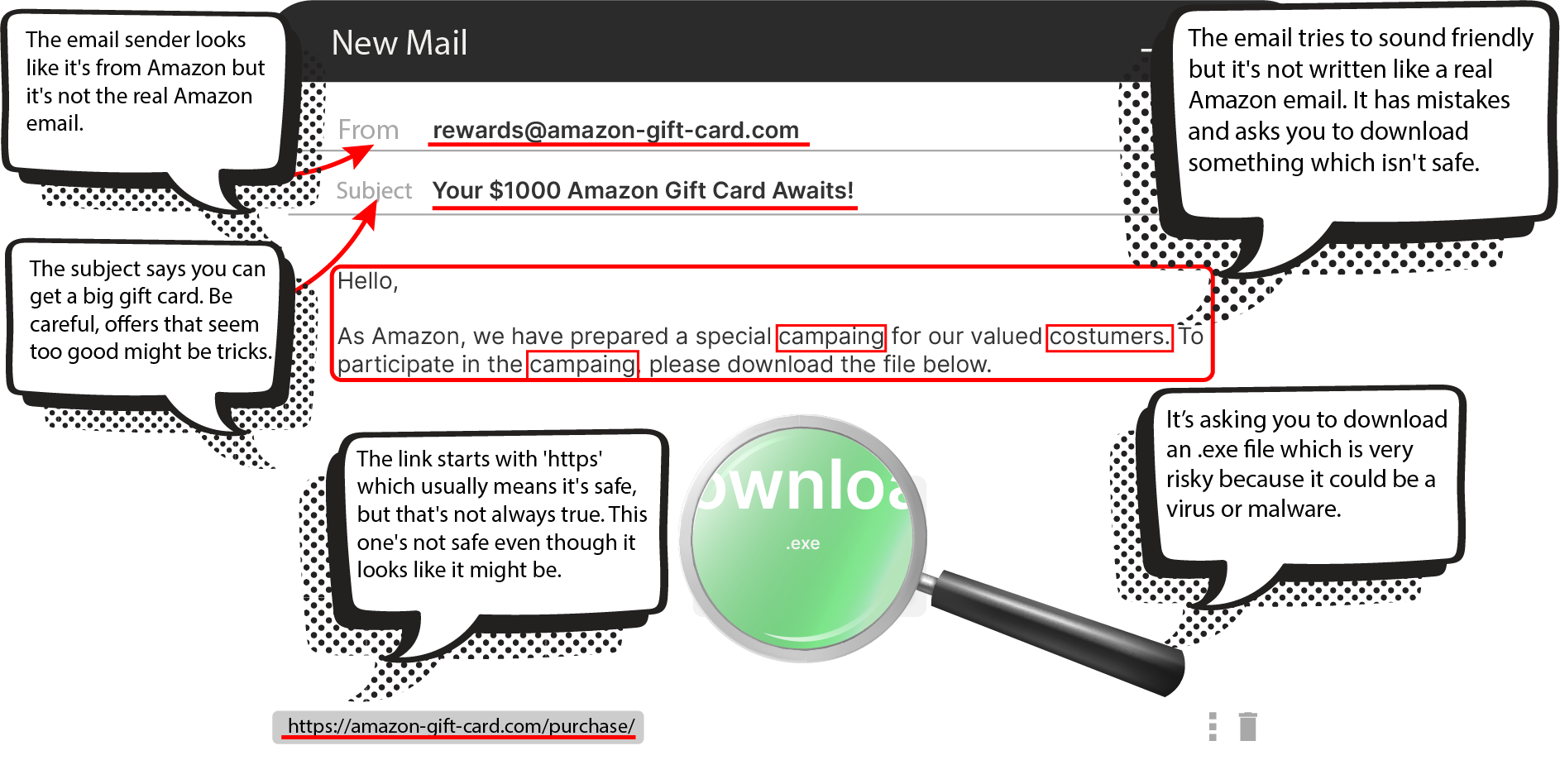
Disguised as credible messages, phishing emails are the trojan horses of the digital world. Phishy's comprehensive training programs arm your team with the critical skills to identify and neutralize these deceptive threats.
User Interaction
The line between security and breach is drawn at user interaction. Phishy's engaging training modules turn every team member into an active participant in your security strategy, ready to spot and stop phishing attacks in their tracks.
OUR VALUE PROPOSITION
Phishy: Crafting Cyber Resilience
Swipe to uncover the 'Before and After Phishy' effect. Our training equips employees with the sharp eye needed to spot and stop phishing threats, transforming them into proactive guardians against cyber attacks.

Proactive Detection
Employees learn to identify threats first-hand, reducing risk and enhancing organizational security.
Behavioral Shield
Interactive training that embeds cybersecurity best practices into daily routines, creating a resilient workforce.
Cultural Transformation
We transform your team's mindset, so every staff member becomes an alert guardian against digital dangers.
Explore Our Cybersecurity Ecosystem
Delve into our specialized modules, each designed to empower your organization with proactive cyber defense strategies. Learn more about each module below and discover how to enhance your team's security posture.
Simulation
Next-Gen Phishing Simulation
Harness the power of Phishy’s simulation suite with over 50 ready-to-use scenarios, or craft your custom simulations with our intuitive drag-and-drop editor—a unique feature that sets us apart. Monitor engagement in real time, tracking email opens, link clicks, data submissions, and file interactions. Plus, conduct simulations through your own mail server, gaining the flexibility to operate under any domain for a truly authentic experience.


Training
Engaging Cybersecurity Training
Elevate your team’s learning experience with Phishy’s gamified video sessions, averaging 2 minutes for maximum engagement without overwhelming your team. Assign specific training modules, track progress, and ensure completion. Non-skippable content guarantees full participation, and our persistent reminder system ensures no one falls behind, fostering a culture of continuous cybersecurity awareness.
Incident Response
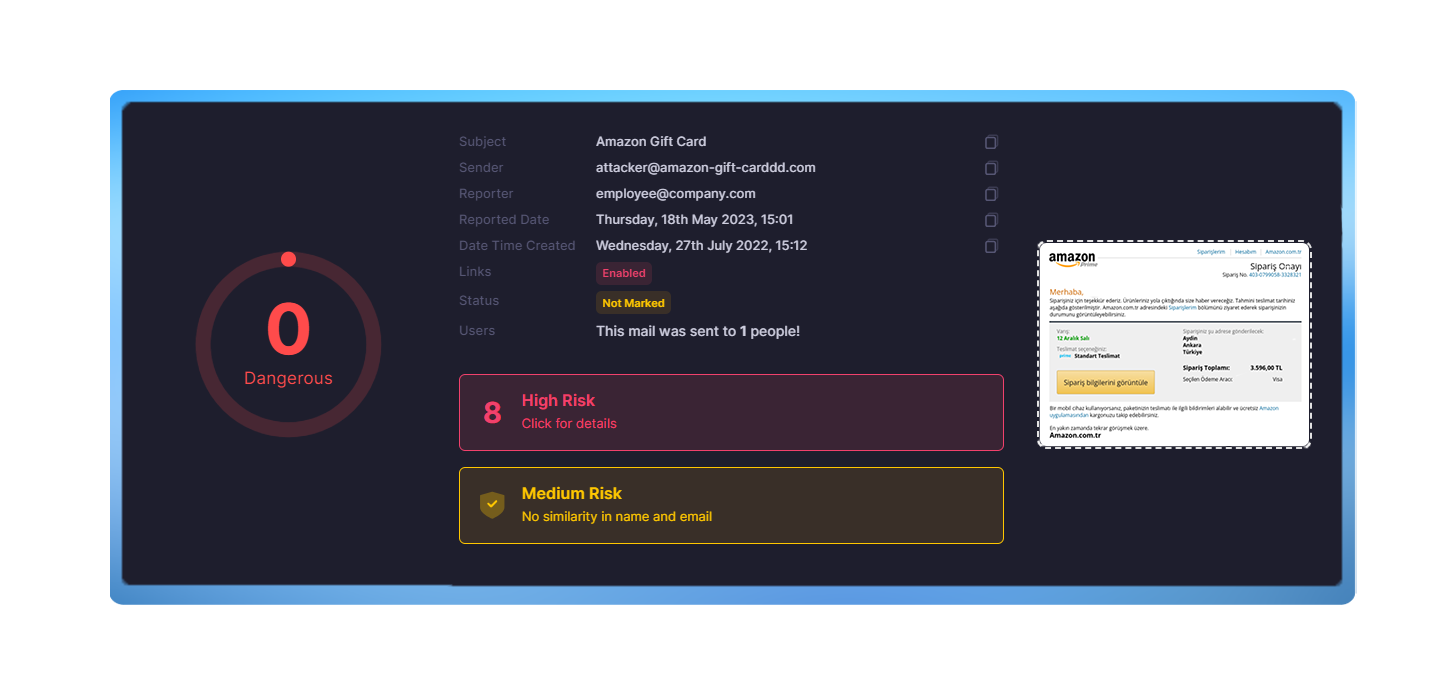
Intelligent Phishing Detection
Phishy’s incident response tool integrates seamlessly with Outlook, enabling employees to report suspicious emails effortlessly. Each reported email undergoes a thorough analysis using our proprietary algorithms and cross-referencing with trusted third-party sources, completing this comprehensive analysis in just 10 seconds. We present the essential information needed for your analysts to determine the legitimacy of an email, streamlining the decision-making process for identifying phishing attacks or false positives.

Phishypot
Advanced Email Honeypot Protection
Empower your cybersecurity defenses with Phishy’s “PhishyPot”—a strategic honeypot email tool designed for proactive threat detection. Clients create and register a decoy email on their own server, which we then strategically expose on hacker forums and dark web sites. This bait attracts potential attackers directly into our surveillance system. PhishyPot continuously monitors these honeypot accounts, instantly analyzing and responding to any malicious activity. Enhance your security measures by turning potential attacks into opportunities for strengthening your defenses.
WHY ENTERPRISES TRUST PHISHY
Proven Trust: The Choice of Industry Leaders
Leading enterprises trust Phishy for comprehensive phishing simulations, immersive training, and dynamic incident response to strengthen their cybersecurity posture
Tailored Simulations
Customizable phishing simulations that mimic emerging threats, preparing teams for real-world attacks
Cutting-Edge Technology
Advanced tools and techniques that keep companies at the forefront of cybersecurity defenses
Strategic Insights
Data-driven insights that inform security strategies and foster a culture of continuous improvement
Scalable Solutions
Flexible and scalable security solutions that grow with your business, ensuring protection no matter the size or scope
Expert Partnerships
A trusted extension of your security team, offering expert guidance and support to navigate the complex cybersecurity landscape
Intuitive Interface
A user-friendly platform that simplifies the complex world of cybersecurity, making it accessible for teams of all tech levels
Rapid Support
Rapid support and proactive assistance ensure your cybersecurity needs are met with speed and precision
Seamless Integration
Effortless integration with existing systems for a smooth and cohesive cybersecurity experience
